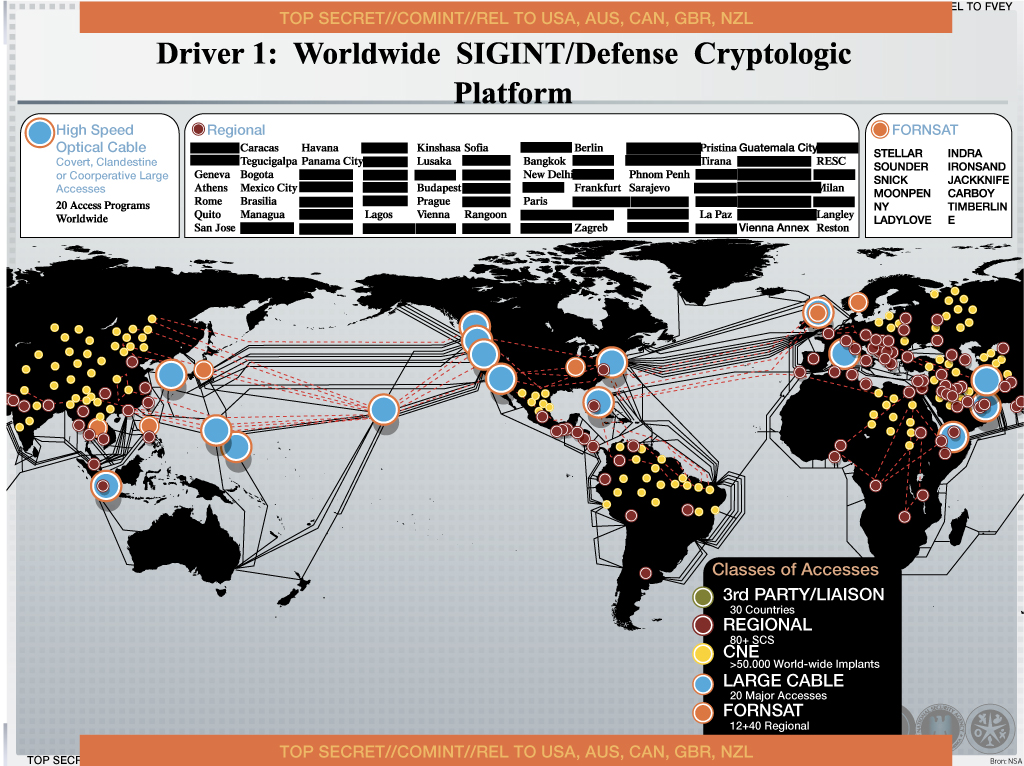
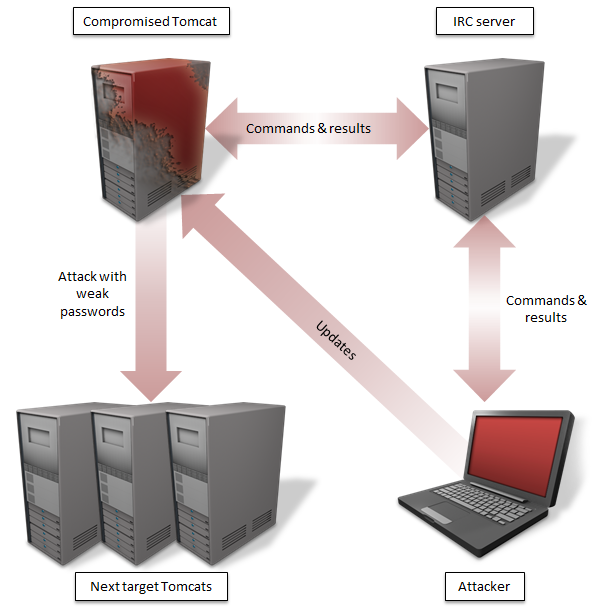
|
According to an article in The Guardian today, Howells threw out the hard drive, "rescued from a defunct Dell laptop," this past summer. "And then last Friday he realised that it held a digital wallet with 7,500 Bitcoins created for almost nothing in 2009," the story notes.
Read 5 remaining paragraphs | CommentsHowells, an IT pro, says his mistake likely occurred in mid-July, at which time a single bitcoin was worth about $90. Today, the value of a single bitcoin passed $1,000 for the first time, making 7,500 bitcoins worth $7.5 million. According to The Guardian story, Howells did not have a backup. The drive he allegedly threw out "contains the cryptographic 'private key' that is needed to be able to access and spend the Bitcoins; without it, the 'money' is lost forever." |
"Dilbert" creator Scott Adams talks to WSJ editor Gary Rosen about how to draw lessons, skills and ideas from your failures—and why following your passion is asking for trouble.
If you're already as successful as you want to be, both personally and professionally, congratulations! Here's the not-so-good news: All you are likely to get from this article is a semientertaining tale about a guy who failed his way to success. But you might also notice some familiar patterns in my story that will give you confirmation (or confirmation bias) that your own success wasn't entirely luck.
Let me start with some tips on what not to do. Beware of advice about successful people and their methods. For starters, no two situations are alike. Your dreams of creating a dry-cleaning empire won't be helped by knowing that Thomas Edison liked to take naps. Secondly, biographers never have access to the internal thoughts of successful people. If a biographer says Henry Ford invented the assembly line to impress women, that's probably a guess.If you're just starting your journey toward success—however you define it—or you're wondering what you've been doing wrong until now, you might find some novel ideas here. Maybe the combination of what you know plus what I think I know will be enough to keep you out of the wood chipper.
But the most dangerous case of all is when successful people directly give advice. For example, you often hear them say that you should "follow your passion." That sounds perfectly reasonable the first time you hear it. Passion will presumably give you high energy, high resistance to rejection and high determination. Passionate people are more persuasive, too. Those are all good things, right?
Here's the counterargument: When I was a commercial loan officer for a large bank, my boss taught us that you should never make a loan to someone who is following his passion. For example, you don't want to give money to a sports enthusiast who is starting a sports store to pursue his passion for all things sporty. That guy is a bad bet, passion and all. He's in business for the wrong reason.
My boss, who had been a commercial lender for over 30 years, said that the best loan customer is someone who has no passion whatsoever, just a desire to work hard at something that looks good on a spreadsheet. Maybe the loan customer wants to start a dry-cleaning store or invest in a fast-food franchise—boring stuff. That's the person you bet on. You want the grinder, not the guy who loves his job.
For most people, it's easy to be passionate about things that are working out, and that distorts our impression of the importance of passion. I've been involved in several dozen business ventures over the course of my life, and each one made me excited at the start. You might even call it passion.
The ones that didn't work out—and that would be most of them—slowly drained my passion as they failed. The few that worked became more exciting as they succeeded. For example, when I invested in a restaurant with an operating partner, my passion was sky high. And on day one, when there was a line of customers down the block, I was even more passionate. In later years, as the business got pummeled, my passion evolved into frustration and annoyance.
On the other hand, Dilbert started out as just one of many get-rich schemes I was willing to try. When it started to look as if it might be a success, my passion for cartooning increased because I realized it could be my golden ticket. In hindsight, it looks as if the projects that I was most passionate about were also the ones that worked. But objectively, my passion level moved with my success. Success caused passion more than passion caused success.
So forget about passion. And while you're at it, forget about goals, too.
Just after college, I took my first airplane trip, destination California, in search of a job. I was seated next to a businessman who was probably in his early 60s. I suppose I looked like an odd duck with my serious demeanor, bad haircut and cheap suit, clearly out of my element. I asked what he did for a living, and he told me he was the CEO of a company that made screws. He offered me some career advice. He said that every time he got a new job, he immediately started looking for a better one. For him, job seeking was not something one did when necessary. It was a continuing process.
This makes perfect sense if you do the math. Chances are that the best job for you won't become available at precisely the time you declare yourself ready. Your best bet, he explained, was to always be looking for a better deal. The better deal has its own schedule. I believe the way he explained it is that your job is not your job; your job is to find a better job.
This was my first exposure to the idea that one should have a system instead of a goal. The system was to continually look for better options.
Read the rest if Scott Adam's article here: