The hard drive isn't the most spectacular bit of hardware, but it's essential to keep your PC running smoothly. If it goes kaput, it takes all of your precious data and your applications with it. So to keep your hard drive happy, healthy and running smoothly by following these straightforward tips.
We're focusing on traditional hard drives here, the large capacity disks more commonly found in desktops and all-in-ones. If you've got a nippy SSD installed in your system then a lot of these points don't apply, as there are no moving parts and data is automatically optimized.
Get rid of what you don't need
If your hard drive is cluttered up with applications you never run and files you never look at, Windows and the disk itself has to work harder to find the information you are interested in. It's a bit like trying to walk barefoot across a floor littered with Lego pieces—it's much easier if everything you don't need has been cleared away.
Applications can be uninstalled from the Control Panel or by right-clicking on their icons on the Start screen. They'll take their settings files, registry entries and other paraphernalia along with them too, leaving you with a much more efficient and lean system that's easier to move around in.
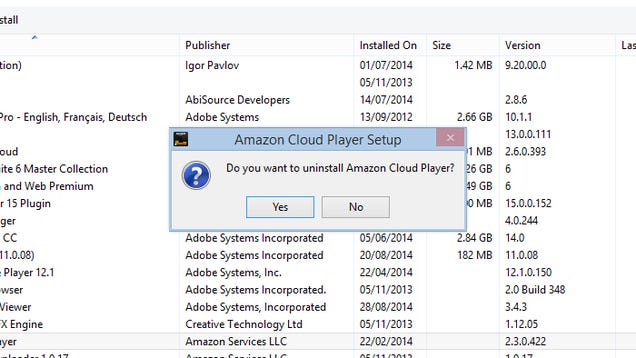
If you want to hire in a professional for the job then Revo Uninstaller and Iobit Uninstaller are two of the best free tools we've seen in this area. They'll really pull up a program by its roots and make sure everything is cleared away, finding temporary files and obscure settings entries that Windows alone might miss. Revo Uninstaller includes a "hunter mode" that zeroes in on applications that aren't listed in the standard programs list.
The same principles apply to personal files too. Clear out junk you don't need for a happier hard drive. This could be anything from a duplicate copy of the Godzilla movie to a setup program that you've finished with. Right-click on your hard drive in File Explorer, choose Properties and you'll find a Disk Clean-up tool that can look for redundant data for you; CCleaner is an excellent third-party freeware program that does a similar job.
Regularly optimize your drive
As time goes by and your hard drive fills up, Windows has to split up files to fit them in on disk. It's a problem that compounds as the weeks and months pass, which is why you need to stay on top of it. Fortunately the operating system takes care of most of this automatically.
Right-click on your drive in File Explorer and choose Properties from the menu that pops up. Open the Tools tab and you'll find a utility for checking for errors on the drive as well as the defrag program—click Optimize to run a manual optimization and to check that Windows is scheduling frequent check-ups of the state of your drive.
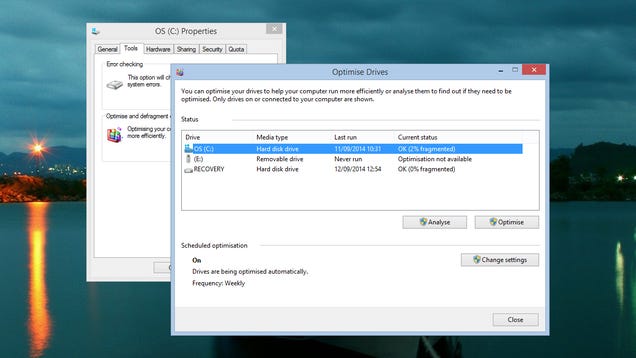
Power options are worth looking into, as well. You wouldn't leave your car idling in the driveway all day, so don't have your hard drive chugging away when it's not necessary. Hard drives don't live forever and you don't want to exert the disks without a good reason. From Control Panel, choose Hardware and Sound and then Power Options to bring up the current power plans.
By default, the hard drive spin down setting (found via Change advanced power settings) is set to 20 minutes of inactivity, which is about right; if you don't take many breaks from your PC then you can reduce this a little, but you don't want to be in a situation where your hard drive is sleeping and waking every time you take your hands away from the keyboard.
Keep it cool
Hard drives love running at room temperature—anything too hot (or indeed too cold) can play havoc with the delicate mechanisms inside the disk unit. Using a laptop in bed brings up quite a few potential problems, one of which is overheating, which can increase the strain on your hard drive and the likelihood of it wilting.
Along the same lines, make sure your desktop, laptop or all-in-one has plenty of room in which to work. Keep those desk cabinets, pot plants and winter scarves at a good distance so that the ventilation systems on your machine can work as they're intended to. If dust starts to build up around the ventilation ports at the sides of your computer then clean it away.
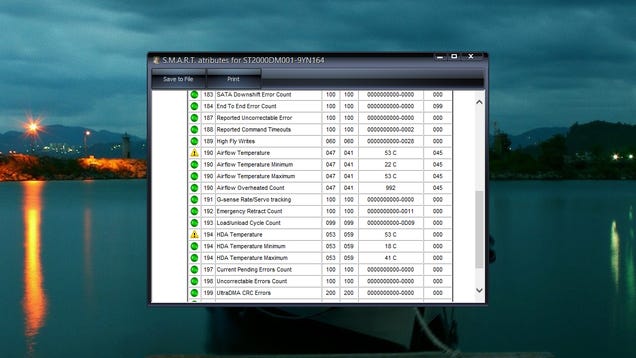
Hard drives are very good at reporting back their current state of health and there are dozens of helpful freeware utilities that can tap into this data. HDDScan is a good option for this, as isSpeccy (from the developers of the aforementioned CCleaner). DiskCheckup is another good option worth checking out and it's free for non-commercial use.
These utilities can report back on the temperature and performance of your installed hard drives, giving you an early warning system if something should go wrong. It goes without saying that you should always have backups in place—but then you already knew that, didn't you?
[Header image: Stockfoto / Shutterstock.com]


 "I'm sorry. Our intentions were good."
"I'm sorry. Our intentions were good."