Nationwide chain P.F. Chang’s China Bistro said today that it is investigating claims of a data breach involving credit and debit card data reportedly stolen from restaurant locations nationwide.
 On June 9, thousands of newly-stolen credit and debit cards went up for sale onrescator[dot]so, an underground store best known for selling tens of millions of cards stolen in the Target breach. Several banks contacted by KrebsOnSecurity said they acquired from this new batch multiple cards that were previously issued to customers, and found that all had been used at P.F. Chang’s locations between the beginning of March 2014 and May 19, 2014.
On June 9, thousands of newly-stolen credit and debit cards went up for sale onrescator[dot]so, an underground store best known for selling tens of millions of cards stolen in the Target breach. Several banks contacted by KrebsOnSecurity said they acquired from this new batch multiple cards that were previously issued to customers, and found that all had been used at P.F. Chang’s locations between the beginning of March 2014 and May 19, 2014.
Contacted about the banks’ claims, the Scottsdale, Arizona-based restaurant chain said it has not yet been able to confirm a card breach, but that the company “has been in communications with law enforcement authorities and banks to investigate the source.”
“P.F. Chang’s takes these matters very seriously and is currently investigating the situation, working with the authorities to learn more,” the company said in an emailed statement. “We will provide an update as soon as we have additional information.”
A spokesperson for the U.S. Secret Service, which typically investigates breaches involving counterfeit credit and debit cards, declined to comment.
It is unclear how many P.F. Chang’s locations may have been impacted. According to the company’s Wikipedia entry, as of January 2012 there were approximately 204 P.F. Chang’s restaurants in the United States, Puerto Rico, Mexico, Canada, Argentina, Chile and the Middle East. Banks contacted for this story reported cards apparently stolen from PFC locations in Florida, Maryland, New Jersey, Pennsylvania, Nevada and North Carolina.
The new batch of stolen cards, dubbed “Ronald Reagan” by the card shop’s owner, is the first major glut of cards released for sale on the fraud shop since March 2014, when curators of the crime store advertised the sale of some 282,000 cards stolen from nationwide beauty store chain Sally Beauty.
The items for sale are not cards, per se, but instead data copied from the magnetic stripe on the backs of credit cards. Armed with this information, thieves can re-encode the data onto new plastic and then use the counterfeit cards to buy high-priced items at big box stores, goods that can be quickly resold for cash (think iPads and gift cards, for example).
The most common way that thieves steal this type of card data is by hacking into cash registers at retail locations and planting malicious software that surreptitiously records mag stripe data when cards are swiped through the machines. The breaches at Target, Neiman Marcus, Michaels and Sally Beauty all were powered by malware that thieves planted on point-of-sale systems.
Unlike with the Target and Sally Beauty batches, however, the advertisement on Rescator’s shop for cards sold under the Ronald Reagan batch does not list the total number of cards that are for sale currently. Instead, it appears to list just the first 100 pages of results, at approximately 50 cards per page. The cards range in price from $18 to $140 per card. Many factors can influence the price of an individual card, such as whether the card is a Visa or American Express card; similarly, Platinum and Business cards tend to fetch far higher prices than Classic and Standard cards.
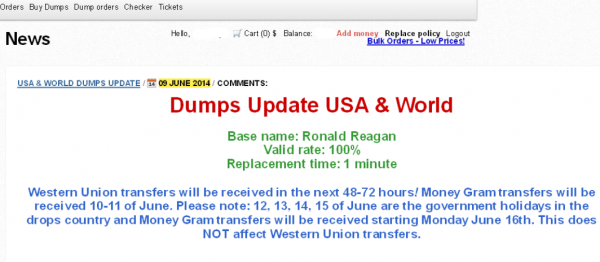 A new ad that debuted on June 9 for a fresh batch of cards apparently stolen from PF Chang’s China Bistro locations.
The ad for the Ronald Reagan batch of cards also includes guidance for potential customers who wish to fund their accounts via Western Union or MoneyGram wire transfers, advice that strongly suggests those involved in this apparent heist are once again from Russia and Eastern Europe:
A new ad that debuted on June 9 for a fresh batch of cards apparently stolen from PF Chang’s China Bistro locations.
The ad for the Ronald Reagan batch of cards also includes guidance for potential customers who wish to fund their accounts via Western Union or MoneyGram wire transfers, advice that strongly suggests those involved in this apparent heist are once again from Russia and Eastern Europe:
It seems likely that P.F. Chang’s only learned of this breach very recently. The cards sold under the Ronald Reagan base are advertised at “100 percent valid,” meaning that fraudsters can expect all of the cards they purchase to have not yet been canceled by the issuing banks. For a deeper dive on how valid rates are a fairly reliable indicator of the recency of a breach, see my analysis of the valid rates on cards stolen in the Target, Sally Beauty and Harbor Freight break-ins.
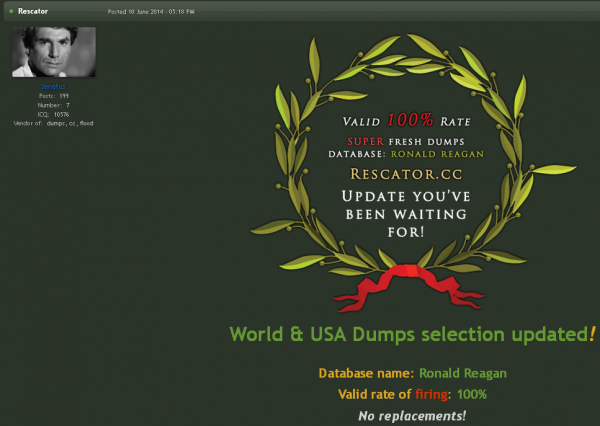 Rescator, a miscreant closely tied to the Target breach, advertises the new batch of cards on his crime forum.
For more information on Rescator, the miscreant apparently responsible for selling (if not also stealing) the cards from this apparent breach, and in the Sally Beauty and Target breaches, see this story.
Rescator, a miscreant closely tied to the Target breach, advertises the new batch of cards on his crime forum.
For more information on Rescator, the miscreant apparently responsible for selling (if not also stealing) the cards from this apparent breach, and in the Sally Beauty and Target breaches, see this story.
 On June 9, thousands of newly-stolen credit and debit cards went up for sale onrescator[dot]so, an underground store best known for selling tens of millions of cards stolen in the Target breach. Several banks contacted by KrebsOnSecurity said they acquired from this new batch multiple cards that were previously issued to customers, and found that all had been used at P.F. Chang’s locations between the beginning of March 2014 and May 19, 2014.
On June 9, thousands of newly-stolen credit and debit cards went up for sale onrescator[dot]so, an underground store best known for selling tens of millions of cards stolen in the Target breach. Several banks contacted by KrebsOnSecurity said they acquired from this new batch multiple cards that were previously issued to customers, and found that all had been used at P.F. Chang’s locations between the beginning of March 2014 and May 19, 2014.Contacted about the banks’ claims, the Scottsdale, Arizona-based restaurant chain said it has not yet been able to confirm a card breach, but that the company “has been in communications with law enforcement authorities and banks to investigate the source.”
“P.F. Chang’s takes these matters very seriously and is currently investigating the situation, working with the authorities to learn more,” the company said in an emailed statement. “We will provide an update as soon as we have additional information.”
A spokesperson for the U.S. Secret Service, which typically investigates breaches involving counterfeit credit and debit cards, declined to comment.
It is unclear how many P.F. Chang’s locations may have been impacted. According to the company’s Wikipedia entry, as of January 2012 there were approximately 204 P.F. Chang’s restaurants in the United States, Puerto Rico, Mexico, Canada, Argentina, Chile and the Middle East. Banks contacted for this story reported cards apparently stolen from PFC locations in Florida, Maryland, New Jersey, Pennsylvania, Nevada and North Carolina.
The new batch of stolen cards, dubbed “Ronald Reagan” by the card shop’s owner, is the first major glut of cards released for sale on the fraud shop since March 2014, when curators of the crime store advertised the sale of some 282,000 cards stolen from nationwide beauty store chain Sally Beauty.
The items for sale are not cards, per se, but instead data copied from the magnetic stripe on the backs of credit cards. Armed with this information, thieves can re-encode the data onto new plastic and then use the counterfeit cards to buy high-priced items at big box stores, goods that can be quickly resold for cash (think iPads and gift cards, for example).
The most common way that thieves steal this type of card data is by hacking into cash registers at retail locations and planting malicious software that surreptitiously records mag stripe data when cards are swiped through the machines. The breaches at Target, Neiman Marcus, Michaels and Sally Beauty all were powered by malware that thieves planted on point-of-sale systems.
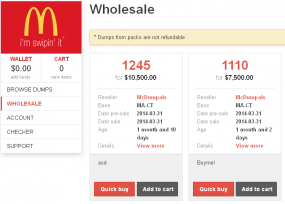
Unlike with the Target and Sally Beauty batches, however, the advertisement on Rescator’s shop for cards sold under the Ronald Reagan batch does not list the total number of cards that are for sale currently. Instead, it appears to list just the first 100 pages of results, at approximately 50 cards per page. The cards range in price from $18 to $140 per card. Many factors can influence the price of an individual card, such as whether the card is a Visa or American Express card; similarly, Platinum and Business cards tend to fetch far higher prices than Classic and Standard cards.
 A new ad that debuted on June 9 for a fresh batch of cards apparently stolen from PF Chang’s China Bistro locations.
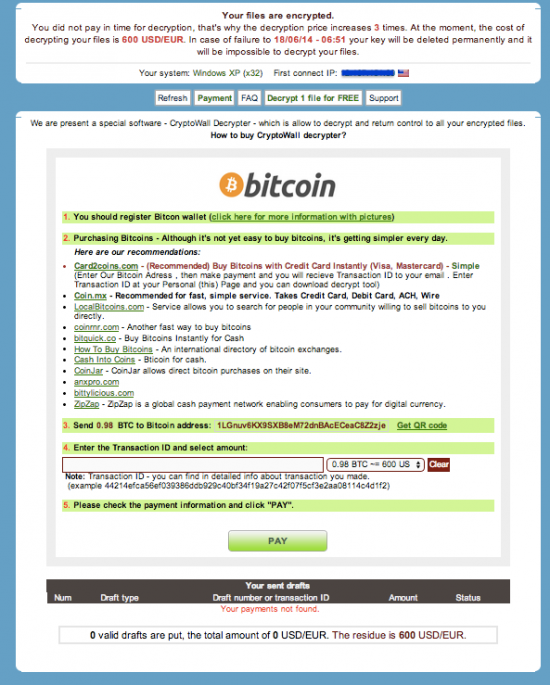
A new ad that debuted on June 9 for a fresh batch of cards apparently stolen from PF Chang’s China Bistro locations.“Western Union transfers will be received in the next 48-72 hours! Money Gram transfers will be received 10-11 of June. Please note: 12, 13, 14, 15 of June are the government holidays in the drops country and Money Gram transfers will be received starting Monday June 16th. This does NOT affect Western Union transfers.”June 12 is “Russia Day,” a national holiday in Russia since 1992 that celebrates the declaration of state sovereignty of the Russian Soviet Federative Socialist Republic on June 12, 1990. “Drops” refers to individuals hired to receive money transfers on behalf of the card shop to help fund new and existing accounts. The shop also accepts payment via Bitcoin (for hopefully obvious reasons, customers cannot pay for the goods using credit cards).
It seems likely that P.F. Chang’s only learned of this breach very recently. The cards sold under the Ronald Reagan base are advertised at “100 percent valid,” meaning that fraudsters can expect all of the cards they purchase to have not yet been canceled by the issuing banks. For a deeper dive on how valid rates are a fairly reliable indicator of the recency of a breach, see my analysis of the valid rates on cards stolen in the Target, Sally Beauty and Harbor Freight break-ins.
 Rescator, a miscreant closely tied to the Target breach, advertises the new batch of cards on his crime forum.
Rescator, a miscreant closely tied to the Target breach, advertises the new batch of cards on his crime forum.