The U.S. Justice Department is expected to announce today an international law enforcement operation to seize control over the Gameover ZeuS botnet, a sprawling network of hacked Microsoft Windows computers that currently infects an estimated 500,000 to 1 million compromised systems globally. Experts say PCs infected with Gameover are being harvested for sensitive financial and personal data, and rented out to an elite cadre of hackers for use in online extortion attacks, spam and other illicit moneymaking schemes.
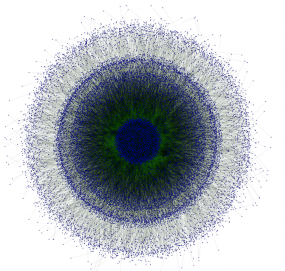 This graphic, from 2012, shows the decentralized nature of P2P network connectivity of 23,196 PCs infected with Gameover. Image: Dell SecureWorks
The sneak attack on Gameover, dubbed “Operation Tovar,” began late last week and is a collaborative effort by investigators at the FBI, Europol, and the UK’s National Crime Agency; security firms CrowdStrike,Dell SecureWorks, Symantec, Trend Microand McAfee; and academic researchers atVU University Amsterdam and Saarland University in Germany. News of the action first came to light in a blog post published briefly on Friday by McAfee, but that post was removed a few hours after it went online.
This graphic, from 2012, shows the decentralized nature of P2P network connectivity of 23,196 PCs infected with Gameover. Image: Dell SecureWorks
The sneak attack on Gameover, dubbed “Operation Tovar,” began late last week and is a collaborative effort by investigators at the FBI, Europol, and the UK’s National Crime Agency; security firms CrowdStrike,Dell SecureWorks, Symantec, Trend Microand McAfee; and academic researchers atVU University Amsterdam and Saarland University in Germany. News of the action first came to light in a blog post published briefly on Friday by McAfee, but that post was removed a few hours after it went online.
Gameover is based on code from the ZeuS Trojan, an infamous family of malware that has been used in countless online banking heists. Unlike ZeuS — which was sold as a botnet creation kit to anyone who had a few thousand dollars in virtual currency to spend — Gameover ZeuS has since October 2011 been controlled and maintained by a core group of hackers from Russia and Ukraine.
Those individuals are believed to have used the botnet in high-dollar corporate account takeovers that frequently were punctuated by massive distributed-denial-of-service (DDoS) attacks intended to distract victims from immediately noticing the thefts. According to the Justice Department, Gameover has been implicated in the theft of more than $100 million in account takeovers.
The curators of Gameover also have reportedly loaned out sections of their botnet to vetted third-parties who have used them for a variety of purposes. One of the most popular uses of Gameover has been as a platform for seeding infected systems with CryptoLocker, anasty strain of malware that locks your most precious files with strong encryption until you pay a ransom demand.
According to a 2012 research paper published by Dell SecureWorks, the Gameover Trojan is principally spread via Cutwail, one of the world’s largest and most notorious spam botnets (for more on Cutwail and its origins and authors, see this post). These junk emails typically spoof trusted brands, including shipping and phone companies, online retailers, social networking sites and financial institutions. The email lures bearing Gameover often come in the form of an invoice, an order confirmation, or a warning about an unpaid bill (usually with a large balance due to increase the likelihood that a victim will click the link). The links in the email have been replaced with those of compromised sites that will silently probe the visitor’s browser for outdated plugins that can be leveraged to install malware.
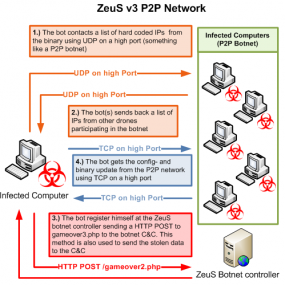
It will be interesting to hear how the authorities and security researchers involved in this effort managed to gain control over the Gameover botnet, which uses an advanced peer-to-peer (P2P) mechanism to control and update the bot-infected systems.
The addition of the P2P component in Gameover is innovation designed to make it much more difficult for security experts, law enforcement or other Internet do-gooders to dismantle the botnet. In March 2012,Microsoft used a combination of legal maneuvering and surprise to take down dozens of botnets powered by ZeuS (and its code-cousin — SpyEye), by seizing control over the domain names that the bad guys used to control the individual ZeuS botnets.
But Gameover would be far trickier to disrupt or wrest from its creators: It uses a tiered, decentralized system of intermediary proxies and strong encryption to hide the location of servers that the botnet masters use to control the crime machine.
“Microsoft’s 2012 takedown action had no effect on the P2P version of ZeuS because of its network architecture,” reads Dell SecureWorks’s 2012 paper on Gameover. “In the P2P model of ZeuS, each infected client maintains a list of other infected clients. These peers act a massive proxy network between the P2P ZeuS botnet operators and the infected hosts. The peers are used to propagate binary updates, to distribute configuration files, and to send stolen data to the controllers.”
According to McAfee, the seizure of Gameover is expected to coincide with a cleanup effort in which Internet service providers contact affected customers to help remediate compromised PCs. The Department of Homeland Security’s U.S. Computer Emergency Readiness Team (US-CERT) today published a list of resources that may help in that effort.
Update, 11:07 a.m. ET: The Justice Department just published a complaint (PDF) that names the alleged author of the ZeuS Trojan, allegedly a Russian citizen named Evgeniy Mikhailovich Bogachev. The complaint mentions something that this blog has noted on several occasions - that the the ZeuS author used multiple nicknames, including “Slavik” and “Pollingsoon.” More court documents related to today’s action are available here.
 This graphic, from 2012, shows the decentralized nature of P2P network connectivity of 23,196 PCs infected with Gameover. Image: Dell SecureWorks
This graphic, from 2012, shows the decentralized nature of P2P network connectivity of 23,196 PCs infected with Gameover. Image: Dell SecureWorksGameover is based on code from the ZeuS Trojan, an infamous family of malware that has been used in countless online banking heists. Unlike ZeuS — which was sold as a botnet creation kit to anyone who had a few thousand dollars in virtual currency to spend — Gameover ZeuS has since October 2011 been controlled and maintained by a core group of hackers from Russia and Ukraine.
Those individuals are believed to have used the botnet in high-dollar corporate account takeovers that frequently were punctuated by massive distributed-denial-of-service (DDoS) attacks intended to distract victims from immediately noticing the thefts. According to the Justice Department, Gameover has been implicated in the theft of more than $100 million in account takeovers.
The curators of Gameover also have reportedly loaned out sections of their botnet to vetted third-parties who have used them for a variety of purposes. One of the most popular uses of Gameover has been as a platform for seeding infected systems with CryptoLocker, anasty strain of malware that locks your most precious files with strong encryption until you pay a ransom demand.
According to a 2012 research paper published by Dell SecureWorks, the Gameover Trojan is principally spread via Cutwail, one of the world’s largest and most notorious spam botnets (for more on Cutwail and its origins and authors, see this post). These junk emails typically spoof trusted brands, including shipping and phone companies, online retailers, social networking sites and financial institutions. The email lures bearing Gameover often come in the form of an invoice, an order confirmation, or a warning about an unpaid bill (usually with a large balance due to increase the likelihood that a victim will click the link). The links in the email have been replaced with those of compromised sites that will silently probe the visitor’s browser for outdated plugins that can be leveraged to install malware.
It will be interesting to hear how the authorities and security researchers involved in this effort managed to gain control over the Gameover botnet, which uses an advanced peer-to-peer (P2P) mechanism to control and update the bot-infected systems.
The addition of the P2P component in Gameover is innovation designed to make it much more difficult for security experts, law enforcement or other Internet do-gooders to dismantle the botnet. In March 2012,Microsoft used a combination of legal maneuvering and surprise to take down dozens of botnets powered by ZeuS (and its code-cousin — SpyEye), by seizing control over the domain names that the bad guys used to control the individual ZeuS botnets.
But Gameover would be far trickier to disrupt or wrest from its creators: It uses a tiered, decentralized system of intermediary proxies and strong encryption to hide the location of servers that the botnet masters use to control the crime machine.
“Microsoft’s 2012 takedown action had no effect on the P2P version of ZeuS because of its network architecture,” reads Dell SecureWorks’s 2012 paper on Gameover. “In the P2P model of ZeuS, each infected client maintains a list of other infected clients. These peers act a massive proxy network between the P2P ZeuS botnet operators and the infected hosts. The peers are used to propagate binary updates, to distribute configuration files, and to send stolen data to the controllers.”
According to McAfee, the seizure of Gameover is expected to coincide with a cleanup effort in which Internet service providers contact affected customers to help remediate compromised PCs. The Department of Homeland Security’s U.S. Computer Emergency Readiness Team (US-CERT) today published a list of resources that may help in that effort.
Update, 11:07 a.m. ET: The Justice Department just published a complaint (PDF) that names the alleged author of the ZeuS Trojan, allegedly a Russian citizen named Evgeniy Mikhailovich Bogachev. The complaint mentions something that this blog has noted on several occasions - that the the ZeuS author used multiple nicknames, including “Slavik” and “Pollingsoon.” More court documents related to today’s action are available here.

I can not help but wonder why, yet again, the public has not been made aware of the ZeuS Trojan. It has been out for several years and yet this is the first I have heard of it. This should have been all over the news with warnings and information about what to look for to prevent it from getting to this large of a threat. Now the government wants to try to take it over? They could not even get a simple website up and running properly, what makes them think they'll be able to take over a botnet?
ReplyDelete