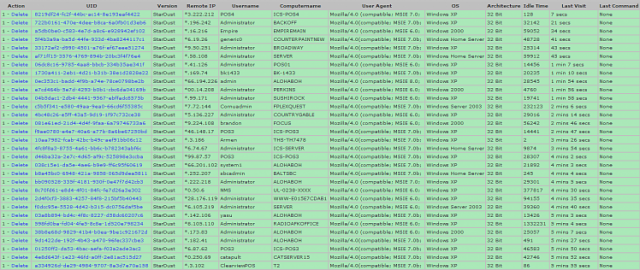
Inside the command and control channel of a point-of-sale botnet powered by StarDust.
IntelCrawler
The botnet remained active at the time of writing and had compromised more than 20,000 payment cards since August, researchers from IntelCrawler, a Los Angeles-based security intelligence provider, told Ars. The researchers arrived at the findings after infiltrating one of the control servers used to send commands to infected machines and receive pilfered data from them. A recently captured screenshot (above) showed that it was controlling 31 machines that the researchers said belonged to US-based restaurants and retailers. Some of the infected machines are servers, so the number of affected PoS devices could be much higher. The researchers have reported their findings to law enforcement agencies that they declined to identify by name.
PoS-based hacking is nothing new. The best-known incident stole data for more than 146,000 cards after infecting 200 terminals used at Subway Sandwich shops and other small merchants. According to federal prosecutors, the criminals behind that intrusion infected one or more servers with "sniffing" software that logged payment card numbers and sent them to a remote server. Although the now-convicted crooks were able to install a backdoor on the computers they accessed so they could change configuration settings and install new programs, there is no evidence of a botnet that actively controlled the infected machines in lockstep.
No comments:
Post a Comment